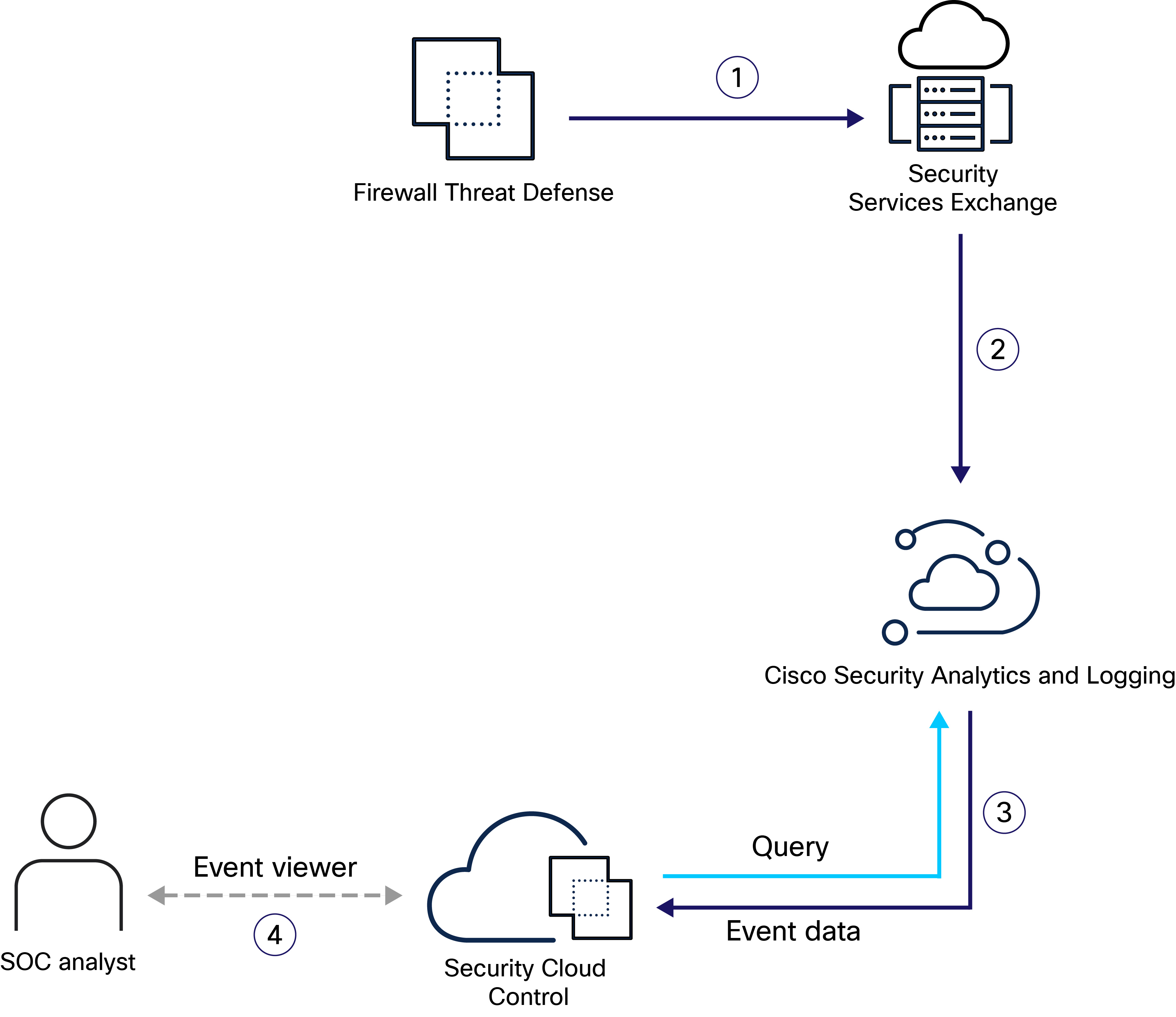
How Firewall Threat Defense Events are Displayed in Security Cloud Control Using a Direct Connection
This diagram describes how Firewall Threat Defense devices that are managed by Security Cloud Control shares security events (connection, security-related connection, intrusion, file, and malware events) with Security Cloud Control.
|
Step |
Description |
|---|---|
|
1 |
You configure the Firewall Threat Defense device to send security events directly to Cisco cloud. Security events are generated when logging is enabled on the Firewall Threat Defense device, and network traffic matches access control rule criteria. The Firewall Threat Defense device sends the events directly to Security Services Exchange. |
|
2 |
Security Services Exchange aggregates the event data from all the Firewall Threat Defense devices, converts it to JSON format, and sends it to Security Analytics and Logging for storage. |
|
3 |
Security Analytics and Logging process the event data using various services to classify and enrich it for use by the Security Cloud Control. |
|
4 |
Security Analytics and Logging stores the event data in the cloud data store. Security Cloud Control queries the stored data to provide SOC analysts with the relevant information. |